Original Blast-RADIUS assault bypasses widely-worn RADIUS authentication


Blast-RADIUS, an authentication bypass within the generally worn RADIUS/UDP protocol, lets in threat actors to breach networks and devices in man-in-the-heart MD5 collision assaults.
Many networked devices (including switches, routers, and other routing infrastructure) on enterprise and telecommunication networks exhaust the authentication and authorization RADIUS (Far-off Authentication Dial-In Consumer Provider) protocol, in most cases tens of thousands of devices on a single community.
Amongst its huge selection of applications, the protocol is worn for authentication in DSL and FTTH (Fiber to the Residence), 802.1X and Wi-Fi, 2G and 3G mobile roaming, 5G DNN (Data Community Name), non-public APN and VPN, and serious infrastructure networks.
Blast-RADIUS exploits a new protocol vulnerability (CVE-2024-3596) and an MD5 collision assault, allowing attackers with salvage entry to to RADIUS web scream online traffic to manipulate server responses and add arbitrary protocol attributes, which permits them to compose admin privileges on RADIUS devices without requiring brute force or stealing credentials.
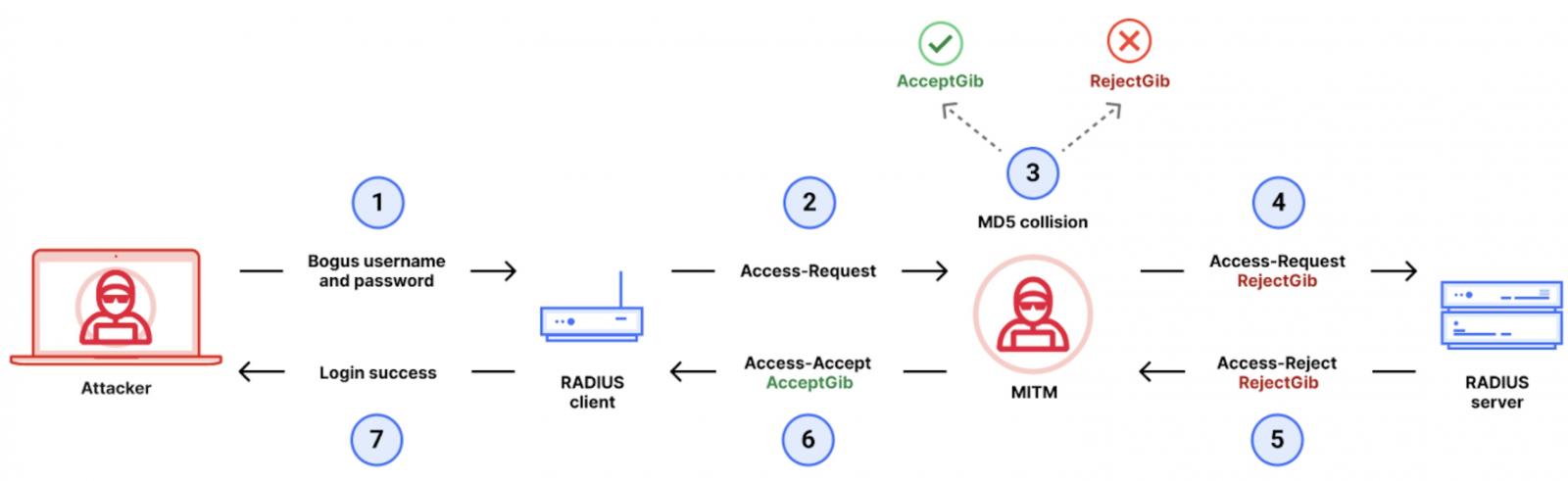
“The Blast-RADIUS assault lets in a person-in-the-heart attacker between the RADIUS client and server to forge a decent protocol accept message in response to a failed authentication are looking ahead to,” the researchers on the assist of itoutlined.
“This forgery would possibly well well give the attacker salvage entry to to community devices and providers and products without the attacker guessing or brute forcing passwords or shared secrets and tactics. The attacker would not be taught person credentials.
“An adversary exploiting our assault can escalate privileges from partial community salvage entry to to with the ability to log into any instrument that makes exhaust of RADIUS for authentication, or to place itself arbitrary community privileges.”
The RADIUS protocol makes exhaust of MD5 hashed requests and responses when performing authentication on a instrument. The researchers’ proof-of-theory exploit (which has yet to be shared) computes an MD5 chosen-prefix hash collision wanted to forge a decent “Assemble entry to-Settle for” response to indicate a a hit authentication are looking ahead to. This forged MD5 hash is then injected into the community verbal exchange the exhaust of the man-in-the-heart assault, allowing the attacker to log in.
The exploit takes 3 to 6 minutes to forge this MD5 hash, longer than the 30—to 60-2d timeouts recurrently worn in apply for RADIUS.
Nonetheless, each and each step of the collision algorithm worn within the assault will be effectively parallelized and is acceptable for hardware optimization, which would enable a smartly-resourced attacker to put in force the assault the exhaust of GPUs, FPGAs, or other more contemporary and faster hardware to raise out noteworthy faster running instances, presumably tens or various of instances faster.
”Whereas an MD5 hash collision became once first demonstrated in 2004, it became once no longer regarded as that you just may presumably presumably think to exhaust this within the context of the RADIUS protocol,” the overview team mentioned.
“Our assault identifies a protocol vulnerability within the skill RADIUS makes exhaust of MD5 that lets within the attacker to inject a malicious protocol attribute that produces a hash collision between the server-generated Response Authenticator and the attacker’s desired forged response packet.
“To boot, because our assault is on-line, the attacker desires with the arrangement to compute a so-known as chosen-prefix MD5 collision assault in minutes or seconds. The old easiest reported chosen-prefix collision assault instances took hours, and produced collisions that had been no longer appropriate with the RADIUS protocol.”
Since this assault would not compromise end-person credentials, there is nothing that end-customers can originate to offer protection to against it. Nonetheless, vendors and machine admins who make and arrange RADIUS devices are counseled to apply these easiest practices and guidance.
To defend against this assault, community operators would possibly presumably make stronger to RADIUS over TLS (RADSEC), swap to “multihop” RADIUS deploymentsand isolate RADIUS web scream online traffic from web salvage entry to the exhaust of restricted-salvage entry to management VLANs or TLS/ IPsec tunneling.






