Fresh Eldorado ransomware targets Windows, VMware ESXi VMs


A new ransomware-as-a-provider (RaaS) known as Eldorado emerged in March and springs with locker variants for VMware ESXi and Windows.
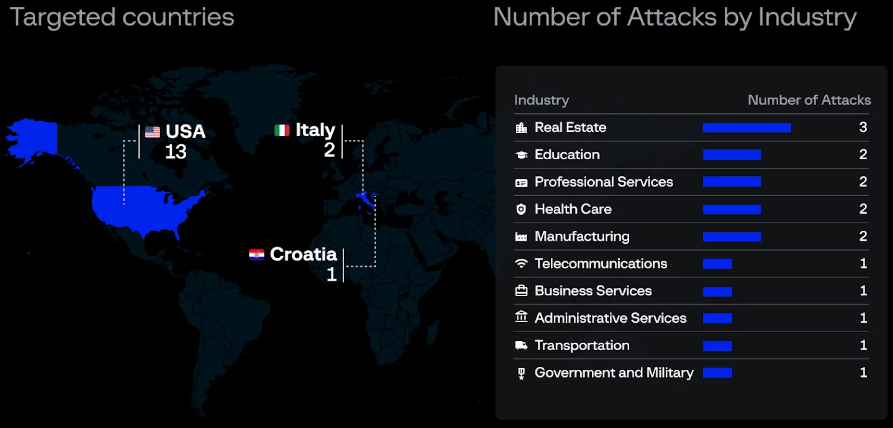
The gang has already claimed 16 victims, most of them within the U.S., in staunch estate, educational, healthcare, and manufacturing sectors.
Researchers at cybersecurity firm Neighborhood-IB monitored the Eldorado’s relate and seen its operators promoting the malicious provider on RAMP forums and seeking educated affiliates to join the program.
Eldorado also runs an data leak set that lists victims however it absolutely was once down at the time of writing.
Offer: Neighborhood-IB
Encrypting Windows and Linux
Eldorado is a Lunge-basically based ransomware that can encrypt both Windows and Linux platforms via two sure variants with wide operational similarities.
The researchers bought from the developer an encryptor, which came with a individual handbook saying that there are 32/64-bit variants on hand for VMware ESXi hypervisors and Windows.
Neighborhood-IB says that Eldorado is a queer type “and does no longer depend on previously revealed builder sources.”
The malware uses the ChaCha20 algorithm for encryption and generates a queer 32-byte key and 12-byte nonce for every and every of the locked info. The keys and nonces are then encrypted using RSA with the Optimum Asymmetric Encryption Padding (OAEP) procedure.
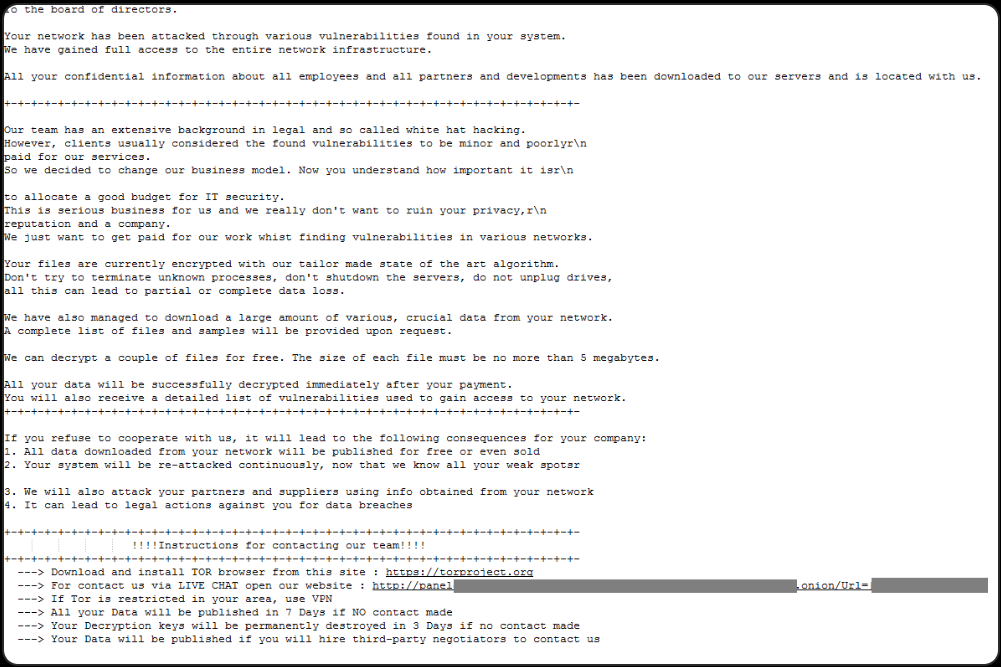
After the encryption stage, info are appended the “.00000001” extension and ransom notes named “HOW_RETURN_YOUR_DATA.TXT” are dropped within the Documents and Desktop folders.
Offer: Neighborhood-IB
Eldorado also encrypts community shares using the SMB verbal exchange protocol to maximize its influence and deletes shadow quantity copies on the compromised Windows machines to forestall restoration.
The ransomware skips DLLs, LNK, SYS, and EXE info, apart from info and directories connected to machine boot and classic functionality to forestall rendering the machine unbootable/unusable.
Lastly, it’s set by default to self-delete to evade detection and diagnosis by response groups.
Based totally totally on Neighborhood-IB researchers, who infiltrated the operation, affiliates can customize their assaults. As an illustration, on Windows they’ll specify which directories to encrypt, skip native info, goal community shares on specific subnets, and forestall self-deletion of the malware.
On Linux, though, customization parameters stop at surroundings the directories to encrypt.
Protection suggestions
Neighborhood-IB highlights that the Eldorado ransomware risk is a brand new, standalone operation that did no longer emerge as a rebrand of one other team.
“Though rather new and no longer a rebrand of notorious ransomware groups, Eldorado has immediate demonstrated its functionality within a temporary time frame to inflict essential hassle to its victims’ data, popularity, and industry continuity.” – Neighborhood-IB
The researchers point out the following defenses, that could per chance attend shield towards all ransomware attack, to a level:
- Put in power multi-facet authentication (MFA) and credential-basically based get hold of entry to solutions.
- Exhaust Endpoint Detection and Response (EDR) to immediate title and reply to ransomware indicators.
- Take data backups steadily to decrease hassle and data loss.
- Remark AI-basically based analytics and evolved malware detonation for staunch-time intrusion detection and response.
- Prioritize and periodically apply security patches to repair vulnerabilities.
- Educate and practice employees to acknowledge and document cybersecurity threats.
- Conduct annual technical audits or security assessments and preserve digital hygiene.
- Chorus from paying ransom as it rarely ensures data restoration and could per chance presumably consequence in extra assaults.